Whether you don’t trust VPN providers, you don’t want to pay for the service or you’re a business that wants to explore a more secure remote access solution for enterprise needs, there are many good reasons to look for a good VPN alternative. Here are seven options to consider – both free and premium – that are often safer and more private than a consumer virtual private network.

Key Takeaways:
- Using a mobile hotspot instead of public WiFi can instantly elevate your privacy.
- Tor and Tor-like services like Brave Browser offer more privacy by routing your traffic through multiple nodes, making tracking harder. However, this comes at the cost of slower speeds.
- For the tech-savvy, setting up your own VPN server provides the maximum security, but it requires more effort to set up and maintain.
- For enterprises, options like Zero Trust Network Access, Secure Access Service Edge, and Software Defined Perimeter provide more robust security than traditional VPNs by verifying identity and granting the least privilege access.
Don’t get me wrong: a consumer VPN is still a great way to facilitate remote network access, stream international Netflix libraries, or protect your online gaming from DDOS attacks.
The fact is that any VPN alternative shared below is going to offer network performance that is far too slow to allow for uninterrupted streaming or gaming. If this is still your use case, then a commercial VPN service like NordVPN (streaming) or ProtonVPN (privacy) is the best way to go.
Consumer VPN Alternatives
If privacy and data protection are your primary objectives, even at the expense of connection speed, then pay attention to each of these next four consumer VPN alternatives.
Use a Mobile Hotspot (instead of Public WiFi)
In the past, you may have heard about the dangers of connecting to the internet at an internet cafe, an airport, or any public WiFi network.
The internet has come a long way since then, and as has been noted in The New York Times, this isn’t a huge risk anymore.
However, if you’re dealing with sensitive data, you work in high-risk fields or you just want to be extra careful, most people forget one of the easiest ways to stay safe on public networks is not to use them. Just use your own.
The easiest way to stay safe on public networks is NOT to use them!
If you didn’t know, most phones nowadays can act as mobile hotspots, allowing you to connect your computer or tablet through your encrypted cellular network.
Simply enter your settings, find “Personal Hotspot”, turn it on, and then connect to the new hotspot on your computer like you would a regular WiFi network. Android devices look slightly different depending on the model, but you’ll be looking for Wireless & Networks within the settings and it’s sometimes called tethering instead of hotspot.
In the end, just ensure you secure your hotspot with a good password and you’re good to go. No need to fear a public network anymore!
Use TOR Browser (or a Tor-like service) for Privacy
If you’re worried about your mobile data limits or you need a more long-term solution, you can always consider something like TOR (The Onion Router) or a Tor-like service that I’ll explain here.
Comparing TOR and VPN is really comparing apples to oranges, and I’ve already gone into detail about the differences between TOR and VPN here
Now TOR isn’t a perfect privacy solution – frankly, nothing is – but it’s the most popular solution for journalists, activists, and others who need to protect the connection between their data and their identity. It works by bouncing your connection through multiple nodes that each doesn’t know the full picture of either where the data came from or where it’s going.
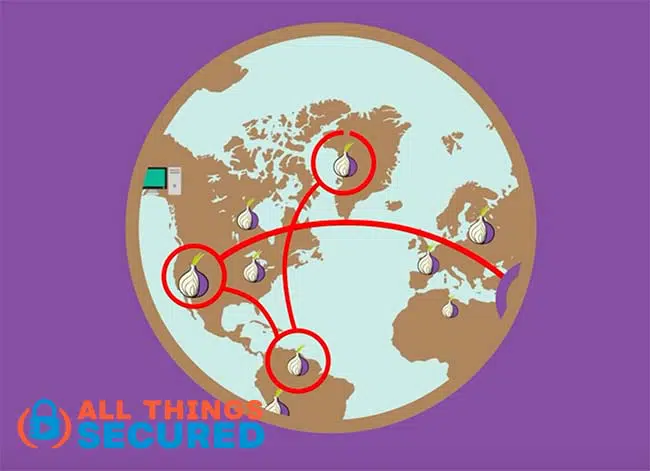
As you can imagine, though, this multi-hop connection makes a noticeable difference in your internet speed.
You can take advantage of TOR or a TOR-like service in these ways:
- Download the TOR Browser: You can visit the Tor Project and download the browser, which will route all internet traffic from the browser through the network.
- Use the Brave Browser: Another great option, and one I recommend is to download the free Brave browser. Not only does it block all tracking and ads, but you can also open a private window with Tor for extra private browsing.
- Use Apple’s Private Relay: With iOS 15, Apple introduced new privacy features including what they call Private Relay. This Private Relay isn’t a VPN, but it acts very much like Tor and it’s worth using if you’re already paying for an iCloud account.
Use a Decentralized VPN (dVPN)
You’re not alone if you’ve never heard of decentralized virtual private networks.
In the same way, Bitcoin offers financial value without the centralized bank, a decentralized VPN, or dVPN for short, offers VPN value without the centralized VPN company. Essentially, you’re crowd-sourcing a peer-to-peer VPN server network, which makes it much harder to track.
You can learn more about decentralized VPNs, and there are a number of options out there, but I’m really impressed with both Mysterium and another popular one called Sentinel.

If you’re looking for a more long-term alternative to a VPN service, this is the one I think is most likely to completely disrupt the entire commercial VPN industry.
Configure Your Own VPN Server
This last option for a VPN alternative is also the most technical and not for the faint of heart. It is possible to set up and run your own VPN, and for free no-less, but the process isn’t nearly as easy as just downloading and connecting to a commercial VPN.
Not by a long shot.
The entire setup process to make your own VPN server will take anywhere between 30 minutes to an hour, but by the end of it, you’ll have your own server that you run and own. No need to worry about who you have to trust with your data.
Enterprise VPN Alternatives
New, secure VPN alternatives are needed more than ever in this hybrid workforce and remote network era. Let’s explore a few contemporary technologies that suit enterprises’ needs better than VPNs.
Zero Trust Network Access
Zero Trust Network Access is part of many enterprises’ security stack. It requires strict identity verification for every user and device trying to access resources on a private network, even if they’re already inside the network perimeter.
Its assumption of breach and verification of every request, never trusting but always validating, is what makes it more robust than a VPN. Users are only granted the least privilege access to specific apps and data needed for their role.
ZTNA authenticates users with strong credentials and evaluates device health and other factors before allowing direct, secure connections to permitted resources. It functions as a proxy gateway instead of opening up the entire network, unlike VPNs.
ZTNA’s identity-based segmentation and granular access controls limit lateral movement post-breach. To implement ZTNA, you require an access broker, an authentication server, and network security changes.
Secure Access Service Edge (SASE)
SASE is a cloud-based security framework that unifies networking and security into a single cloud service. It offers secure identity-based access management to applications and resources, regardless of location. SASE combines SD-WAN, firewalls, zero trust network access, cloud access security brokers, and more into one cloud-native service. This eliminates security gaps while providing seamless and secure access.
It uses context-based policies to confirm user identity, device health, and other details. All internal network traffic is then routed through the SASE cloud, where it is reviewed and secured. SASE streamlines operations with unified networking and security delivered from the cloud. Implementation requires integration with identity providers and migrating security controls to the SASE architecture.
Software Designed Perimeter
Software Defined Perimeter is a security framework that creates a logical network boundary around authorized users and resources. It cloaks applications and infrastructure, making discovery impossible until explicitly accessed.
SDP verifies user and device identity before granting direct, encrypted data access control via secure tunnels rather than open ports. This limits threats and reduces the attack surface.
Furthermore, SDP can layer on top of legacy infrastructure to dynamically segment access privileges. It profiles users and devices, restricting access if suspicious activity is detected. It’s an ideal VPN solution for enterprises wanting to limit exposure and block lateral movement while maintaining productivity.
To employ SDP, you must set up SDP controllers to enforce rules and gateways to enable connections.
Remember: When it comes to your privacy and security, be proactive, not paranoid.


