Tor or VPN? The truth is, it’s not an apples to apples comparison, and since you really care about your privacy and security online, in this article I’m going to provide a basic explanation of how each of these tools work and the specific jobs they’re built for.

There’s one important question you need to ask when comparing Tor vs VPN. It’s quite simple really:
Is your reason for using this kind of privacy technology to keep you from getting in trouble?
If the answer is yes, then Tor is probably your best option. If your answer is no, then a VPN might be recommended here.
And when I say “trouble”, I’m not talking about illegal activity, I’m specifically referring to…
- …dissidents in places like China or Russia fearing political backlash;
- …journalists looking to protect sources;
- …or whistleblowers hoping to protect themselves.
Because as an average internet user, you need to be honest with yourself here: true security and anonymity is impossible unless you abandon the internet altogether.
So everything else is best measured not in binary terms – yes this is private, no this is not private – but rather measured in degrees of strength.
And that’s why a nuanced answer is necessary when comparing Tor vs VPN.
Now I’m going to provide an overview comparison between Tor vs VPN, and then offer one more lesser-known solution that combines the strengths of both of these tools into one.
Note: Some of the links in this article may be affiliate links, which means that at no extra cost to you, I may be compensated if you choose to use one of the services listed. I only recommend what I personally have used, and I appreciate your support!
What is the TOR Network? (The Onion Router)
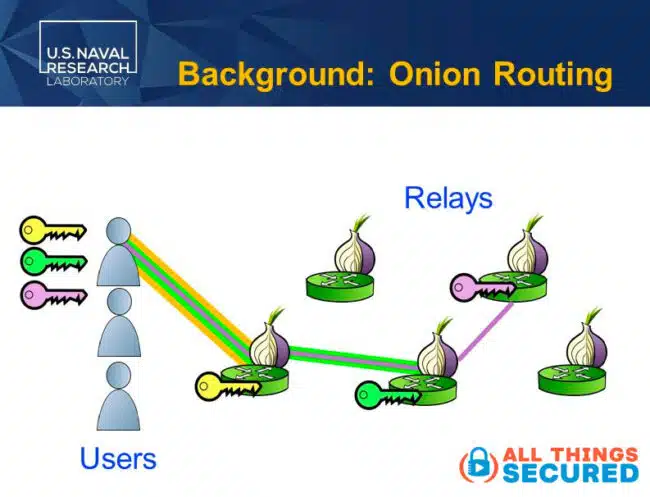
Tor, also known as The Onion Router, takes its name from the way in which it transmits data in layers in order to create online anonymity.
When using something like the Tor browser, your data – including identifiable information such as Tor users IP address – wraps it up in multi-layered encryption and sends it through a network of randomly selected relay servers, each of which only knows their small portion of the journey and not the entire entry to exit transfer.
Tor encrypts your web traffic, hides your original IP address and any trace of your identity.
Where did Tor Originate?
Originally, Tor was developed by employees of the US Naval Research Laboratory in the mid-1990s in order to create an encrypted tunnel to secure messages being sent.
In order for Tor connections to be private, it had to be accessible to the general public. Not only would this boost the number of tor nodes, it also allowed intelligence officers to blend in with other traffic for greater online security.
In the early 2000s, the US Navy cut ties with the Tor network, even though it is still funded and used by the US government.
Example: How TOR Works
Let me give you another example to help explain this better.
Imagine that I want to send a top-secret message to my parents without them knowing it was me who sent it. I wrap it up in another envelope addressed to a different friend and don’t put my return address on it.
- Mailman (1st node): When I give this envelope to the mailman, he doesn’t know where the letter will ultimately end up, he just knows to deliver it to my friend.
- Friend Middleman (2nd Node): When my friend receives the envelope, he doesn’t know where it came from since it has no return address, all he knows is that when he opens it up, there are instructions to give it to my parents.
- Parents (Exit Node): When my parents receive the message, all they know is that it came from my friend, but won’t have any information as to the origin of the message. Spoiler alert: unless I sign my name to it.
That is how Tor creates online privacy, bypassing censorship and obfuscating internet traffic.
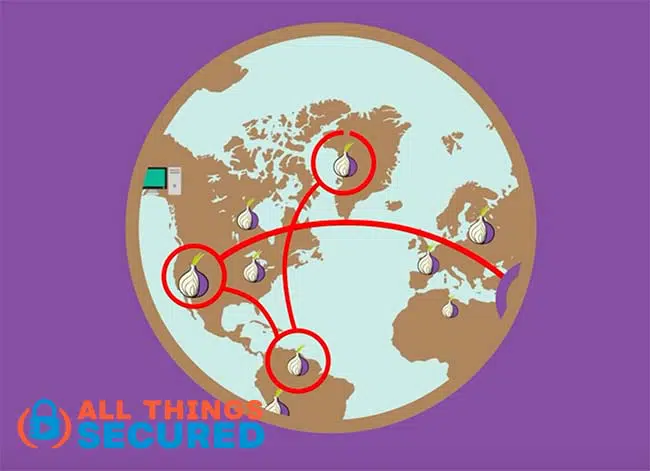
This approach provides a lot of online anonymity, and as far as the Tor vs VPN comparison is concerned, is the best option for those who are truly concerned about somebody following their internet traffic.
Weaknesses of Using TOR Browser
But the Tor browser does have weaknesses. Let’s take a look at a few of them.
- Tor Browser is Slow: Using the Tor browser is noticeably slow, and that makes sense if you consider all that’s happening with the internet traffic when it passes through the Tor encrypted tunnel. So if you’re wanting to stream video content online, download large files, or do anything other than basic internet browsing or messaging, Tor is going to be frustrating to use.
- Tor Traffic is Known: Because The Tor Project publishes the full list of of every exit node, there are many online services that either block access to their website for anybody that comes from an exit node IP address, or they force repeated security challenges such as CAPTCHA and others measures. This means that when using Tor browser, instead of having freer access to the internet, you may find yourself a bit more restricted.
- Limited Privacy Coverage: For the average internet user, the only way you’re going to access the Tor network is via the Tor browser. This means that any other app or data transfer on your device that doesn’t go through this browser does not receive the privacy benefits of the Tor network. A system-wide or device-wide decentralized network is possible, but it’s not going to be easy to set up for the average person.
- It’s not 100% Private: And finally, as I preach over and over on All Things Secured, no tool is 100% secure or 100% private, and there are still ways to pierce the veil of anonymity in the Tor network. Over the years, various security consultants and researchers have claimed ways to compromise the integrity of the Tor network.
Mind you, unless your communications are high value, it’s unlikely anybody would make the effort to do this. The more likely scenario is that you compromise yourself by sending along identifiable data, almost as if I had signed the letter to my parents.
It completely defeats the purpose of me sending an anonymous message in the first place.
The Tor Network is Free
One more benefit that makes Tor users proud:
Tor is free (which is definitely a bonus). When you let the Tor browser hide your web traffic, you’re taking advantage of the volunteer network of nodes and an exit node.
This reliance on volunteers is precisely why the network hasn’t grown very fast over the past decade and it brings up legitimate concerns about who owns both Tor entry nodes and exit nodes and why they’re willing to absorb the cost of running them for free.
What is a Virtual Private Network (VPN)?
So what’s the difference when you compare Tor vs VPN, or virtual private network?
Well, to start, a VPN service wasn’t designed to be a privacy tool. Even for those who wonder if you can be tracked while using a VPN…the answer is yes. It was initially designed as a way to securely connect to a remote server.
This is often used by companies to allow remote employees or offices to plug into the primary company network, but the idea has since grown to include individuals like you and me who want to either hide our IP address, gain privacy from our internet service providers or connect to the internet from a different location.
And that’s really what a VPN service does best: hide your IP address and changing your perceived geolocation.
I mean, there is an additional layer of encryption that happens between you and the VPN server you connect to, but once your internet traffic leaves that VPN tunnel, the encryption is also gone, so take that for what it’s worth.
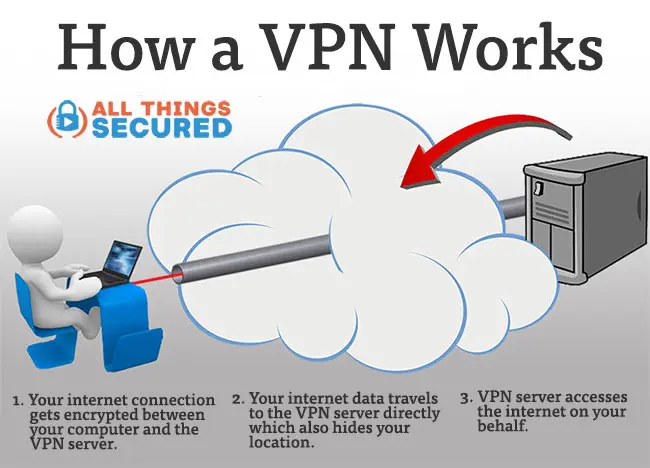
This is why it bothers me that so much of the VPN industry and many of the influencers and content creators who make money here, tend to promote privacy and security as the primary selling points of a VPN. This isn’t the sign of reputable VPN providers.
As I’ve made clear in the past, the truth is that a VPN apps best used to evade censorship, protect your IP address and or access georestricted content like Disney+, BBC iPlayer and more.
Advantages of VPN over Tor
Unlike Tor servers, a VPN providers allow you to easily choose your exit node, which is better when trying to stream this kind of blocked content. You can configure a router with a VPN to control this node and stream content from any device.
VPN services are also significantly faster for streaming content and easier to use. It’s not just on web browsers, either; a VPN encrypts the entire internet connection on your device.

On one hand, VPN encryption is extremely difficult to break, but on the other hand, using a VPN service to hide your IP address or for bypassing censorship is simply a shift of your trust away from your internet service provider and into the hands of the VPN provider.
Most of these VPN providers seek to earn that trust through independent audits and no logs claims, but the truth is that the promise is just that: a promise. And there’s always a risk it could be broken.
I’m comparing Tor vs VPN side by side here, but as I said at the very beginning, this really isn’t an apples to apples comparison. We’re comparing a decentralized network tool, Tor, with a centralized VPN server.
If your data presents a danger to you, Tor is probably your best option. For everything else, a VPN provider probably does everything you need.
Alternatives to Tor and VPN for Privacy
But hold on!
Both Tor and VPN services have been combined in two different ways to build on the strengths of each and minimize their weaknesses. Let’s take a quick look at some alternatives to Tor and VPN.
Tor / Onion Over VPN
First, there’s what’s known as Tor over VPN, also called “Onion over VPN”, where you’re basically connecting to a VPN server first and then accessing the Tor network from there.
It hides the fact that you’re using Tor and prevents any of the Tor exit nodes from seeing your home IP address, if for some reason that matters to you.
This is a popular option that is often native to some VPN services. You’ll find advanced connections that give you the option to route your VPN connection through the Tor network.
VPN “Multi-Hop” Connections
For some VPN software there is something known as a VPN multi-hop connection, or a “double VPN,” which connects across multiple servers instead of just a single VPN server.
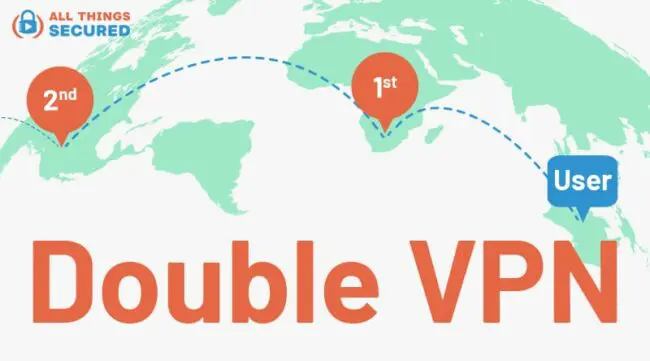
The VPN company still controls each remote server, so it’s not a decentralized option, but it does build added online privacy in case a single server is compromised. This is not a feature that you’ll find with any free VPNs, so check our VPN comparison reviews to find out which ones offer it.
The downside here is, again, slower speeds and a trust in a centralized network.
Decentralized VPN = “dVPN”
The final option that I like more is a decentralized VPN, or dVPN for short.
This is a fascinating technology that combines the speed and control of VPN servers with the privacy and decentralization of Tor. You’re still hiding your IP address and encrypting the online traffic, but you’re doing so without a centralized service in the middle.

It’s also run by a network of volunteer nodes, but since they get paid for the bandwidth they provide using crypto, there’s an understandable incentive for the growth of these virtual private networks.
I use a service like Mysterium Network as my preferred dVPN and while it’s still a technology in its infancy, it has performed well for me.
Tor vs VPN: Which Should You Use?
Ultimately, I’m not here to declare a winner between Tor vs VPN or to tell you that you need to use one over the other to secure your internet connection.
The best way to understand which you should use is to ask yourself the following questions:
- Do I need to hide more than my real IP address?
- From whom do I want to secure my internet connection?
- Do I trust a VPN company to handle my data?
What I hope is that you now have a basic understanding of how both Tor and VPN work and can therefore make the best choice based on how you plan to use them.