Encryption is a method of securing data as it travels from the sender to the receiver over the internet. With end-to-end encryption, all internet traffic or messages are scrambled and can only be unscrambled when it reaches the desired destination. For those who are asking how to encrypt your internet connection…this is how.

Encryption converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext in order to protect sensitive data.
Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not prevent interference; rather, it stops a would-be interceptor from gathering any useful, intelligible data.
There are many reasons why someone would want to encrypt their internet traffic, including:
- Shielding their online activities from their internet service provider;
- Protecting their data from cybersecurity threats;
- Communicating personal information via secure messaging apps;
People’s right to a free, uncensored internet is being debated as nations and companies block access to specific software and hardware applications.
End-to-end encryption can help users utilize any Wi-Fi network or any internet service provider while protecting their privacy and data from any security threats. But, to know how to encrypt your internet traffic, you must first understand why internet encryption is essential.
Why is Encryption Important?
The world wide web was initially designed as a sharing platform, not to be a secure platform. It is open to anyone to do anything.
This open invitation poses a significant risk to internet users who just want to freely access news and information.
By encrypting your internet connection, you’re making yourself immune to several types of online threats, including ISP monitoring, hackers with malicious intent, and even government organizations that collect data from citizens.
To ensure privacy, it’s necessary to have your internet traffic encrypted with at least some kind of data encryption and for your communications to be done through encrypted messaging apps.
Types of Encryption
Did you know that there are various kinds of encryption for your internet traffic? Most people aren’t aware of kind of security measures that are being used to store or transfer their data, but here are the most common.
DES Encryption
The most standard of encryptions in the 1970s, DES encryption is no longer considered to be safe on its own. It encrypts just 56-bits of data at a time and it was found to be easily hacked not long after its introduction. It has, however, served as the standard upon which future, more secure encryption tools were based.
3DES
Triple Data Encryption Standard (3DES) works as its name implies. Instead of using a single, 56-bit key, it uses three separate 56-bit keys for triple protection, hence the “triple data encryption standard” name. The drawback to 3DES is that it takes longer to encrypt the internet traffic. Also, the shorter data block lengths are encrypted three times, but they can still be hacked.
AES Encryption
One of the most secure encryption types, Advanced Encryption Standard (AES) is used by governments and security organizations as well as everyday businesses for classified communications. AES uses “symmetric” key encryption. Someone on the receiving end of the data would need a key to decode it.
AES differs from other encryption types in that it encrypts data in a single block, instead of as individual bits of data. The block sizes determine the name for each kind of AES encrypted data. Most of the data tools available on the market today use AES encryption. Even those that allow you to use other methods with their programs recommend the AES standard.
RSA Encryption
Another popular encryption standard is “Rivest-Shamir-Adleman” or RSA. Widely used for data sent online and relies on a public key to encrypt the data so that those on the receiving end of the data will have their own private key to decode the messages.
RSA Encryption has been proven to be a secure way to send information between people who may not know each other and want to communicate without compromising their personal or sensitive data.
How to Secure Your Internet Connection
If all of those acronyms seem ridiculously confusing, you’re not alone! Thankfully, your understanding of the different types of encryption aren’t as important as your implementation of these advanced security features.
In order to encrypt your internet connection, it’s best to consider all the ways in which you actually connect to the internet.
From your home internet service, email, and other devices, it’s important to make sure that you are protected. In order to secure your internet connection, let’s look at seven specific places you need to secure:
- Home Wireless Network
- Encrypted Email Services
- Internet Browser
- Public Network Traffic (using a VPN or TOR)
- Instant Messaging Apps
- Document & Data Storage
Securing Your Home Wireless Network

Your home networks might have a range of wireless devices on them, from computers and phones to IP cameras, voice assistants, smart TVs, and connected appliances. Taking some basic steps to secure your home Wi-Fi network will help protect your devices from getting hacked or your information from being stolen.
You can encrypt your home network by simply updating your router settings to either WPA3 Personal or WPA2 Personal.
WPA3 is the newest encryption available, but both will work to scramble your information.
In addition to this kind of robust encryption solution, other ways to secure your home Wi Fi network include:
- Changing the router password
- Stopping the SSID broadcast (in the wireless router settings)
- Setting up a VPN connection on your router (so all your internet traffic is encrypted and it hides your router’s IP address)
Encrypted Email Security and Protection
Email encryption is mixing up the contents of an email so it becomes a puzzle that only you have the key to solve. The public key infrastructure (PKI) is used to encrypt and decrypt emails. Each person is assigned public and private keys in the form of digital code.
Email providers like Gmail, Yahoo or Outlook do a basic job of encrypting email messages at rest and at transit, but they do not offer end-to-end encryption.
The best encrypted mail providers encrypt all messages, not just the ones with sensitive information. Sensitive information such as social security numbers, passwords, login credentials, and bank account numbers are vulnerable when sent via email, but only having select emails encrypted is a red flag for hackers and can leave you even more vulnerable.
Here a the types of email encryption that are available:
- S/MIME: Secure/Multipurpose Internet Mail Extensions is built into most OSX and iOS devices and relies on a centralized authority to pick the encryption algorithm. S/MIME is used most often because it is built into large web-based email companies such as Apple and Outlook.
- PGP/MIME: Pretty Good Privacy/Multipurpose Internet Mail Extensions relies on a decentralized trust model and was developed to address security issues facing plain text messages. Within this model, there is more flexibility and control over how well you want your emails to be encrypted, but it requires a third-party encryption tool.
I use and recommend a secure email service called Proton Mail, which is widely considered one of the best available.
Internet Browser Security & Privacy
Running a secure internet browser has gone from an option to a virtual necessity in recent years, especially if you want to encrypt your internet connection.
Attackers will constantly seek ways to steal information sent between users and web services, often by tapping into unencrypted content being sent with your regular internet traffic.

Even for mundane, untargeted web content, securing a website with encryption is crucial, as the top browsers now flag unencrypted websites as potentially dangerous.
- HTTPS: “Hypertext Transfer Protocol Secure” When it comes to web traffic, https is different from https in that it enables website encryption by running HTTP over the Transport Layer Security (TLS) protocol. Even though the SSL protocol was replaced 20 years ago by TLS, these certificates are still often referred to as SSL certificates.
While these sessions can be reliably considered secure from eavesdropping attacks, HTTPS (hypertext transfer protocol secure) by itself does not protect against any other types of attack.
Site administrators must still take an active role in preventing and mitigating cross-site scripting, injection, and many other attacks that target application or other website vulnerabilities.
VPN – Virtual Private Network & Tor Browser
A VPN connection, short for Virtual Private Network, acts as a secure route for your internet traffic to a trusted third-party VPN server. All data sent through this route gets encrypted, making it harder for third parties to identify and target individual users on a network.
Commerical VPNs are available for a monthly fee. These VPN services are easy to set up for business or personal use and can easily encrypt your internet connection with the click of a button. A VPN doesn’t hide your location, but it does mask your IP address.
Once you’ve established VPN encryption, your real IP address is changed to a different IP address that corresponds to another location. This way, no third party can identify you, as your digital footprint and location are encrypted.
The TOR browser, on the other hand, is a powerful encryption browser that hides your activities from ISPs, and an online routing system that will encrypt your internet traffic by bouncing it across multipl “nodes,” called the TOR network.
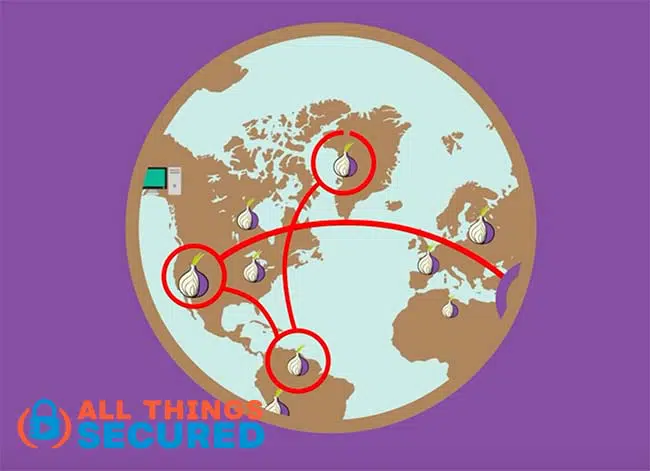
At each hop, only the last and next IP addresses are available to enable routing. The other hops, including the real one, are encrypted and can only be decrypted by a Tor router.
When comparing TOR vs VPN, there are a number of differences including:
- The TOR browser sends your traffic through multiple nodes to provide protection via layers.
- Using TOR browser affects internet speed, as it is much slower than VPN traffic.
- The TOR Browser only protects your browser-based online traffic, not the internet activity of the entire device.
Encrypted Instant Messaging
Some messaging apps use end-to-end encryption (E2EE) while others just use standard web encryption. The former encrypts messages from the sender to the receiver without allowing third parties to intercept them.
Both the sender and the receiver have public and private keys needed to decipher the message. The message can only be unlocked if you have both keys. This doesn’t encrypt your internet traffic, per se, as much as the messages themselves.
Not all IM services support E2EE (such as Facebook Messanger), instead defaulting to an older data encryption standard. It’s important to choose privacy-oriented encrypted messaging services that do use E2EE encryption.
We recommend:
- Signal: The most popular of the encrypted messaging apps
- WhatsApp: Although owned by Facebook, WhatsApp does boast an end-to-end encryption algorithm
Both of these applications are designed to deliver end-to-end encryption, which protects your data from would-be hackers.
Organizations use sophisticated algorithms to suggest ads and search engine queries. The information that you share when you communicate with internet data should be kept confidential with end-to-end encryption.
Securing Document & Storage
Document encryption is the process by which documents are protected with cryptographic keys (a password, public key, token, etc.) so that only individuals with the corresponding decryption keys (the same password, private key, token, etc.) can open them.

This kind of encryption algorithm is used to protect documents sent via email, stored on a disk, or in the cloud from being accessed by unauthorized users.
Document encryption programs can either be standalone applications (like PGP, which encrypts any files and not just documents) or plugins to certain applications like MS-Word or Adobe Acrobat which enable documents to be encrypted when they are saved to disk.
While most document encryption programs provide NIST-approved AES encryption they vary with their protection methods. Many provide password protection, others use hardware tokens, whereas others provide public key technology (PKI).
Protect Yourself Online
In this day and age, it’s important to understand how to encrypt your internet traffic to avoid spying from government surveillance agencies and hackers.
Fortunately, you can easily encrypt internet traffic with minimal effort, but there are other ways to consider building greater privacy and security for yourself.
- Use Email Aliases: Instead of giving out your real email address whenever required, email alias services allow you to create unique email addresses for every product or service.
- Hide your Home address: Instead of giving out your personal data, you can use a virtual address to hide your home address since it receives and handles mail on your behalf.
- Use a 2FA Security Key: Having a strong password is the first step to securing your online accounts, but adding a second form of authentication via a 2FA key from Yubico is just as important.

