Have you ever wondered what information about you is available online? A quick Google search of your name and hometown may reveal more data than you’d want. It’s time you start protecting your online privacy!

But now how to protect your privacy online? In the age of information, personal data has become a valuable commodity, and its protection is crucial. From targeted advertising to cyber attacks, individuals are vulnerable to a range of threats that can arise from compromised online accounts.
In this guide, I’ll delve into the significance of online data privacy and share some ways to protect your personal information in the digital realm.
Online Data Privacy: A Myth or Reality?
Online data privacy is an intricate challenge that needs to be addressed. Every website is out to get every little data about its target audience to understand their needs.
Your online privacy is at risk largely because data has value. Advertisers can generate significant revenues by knowing your browsing patterns or search history. For instance, your simple Google search for new apartments can act as a lead for these advertisers to serve you with ads for home insurance, furniture, and security systems.
Although that’s a permissible use of data, some criminals openly steal and trade credit card details on the dark web.
In order to protect your online privacy, you need to accept that this issue isn’t a myth and it is important.
Why is Data Privacy Important?

The significance of data privacy becomes crystal clear when you compile a list of personal details you’re willing to share with random strangers and those you’d prefer not to disclose. You don’t want your bank statements, medical records, or even some of the goods in your shopping cart to be readily available for anyone to see.
There’s a good chance you also don’t want burglars to know the precise time you’ll be absent so they may break into your flat. You might also not want to hand out your data, like date and place of birth, to obtain loans in your name.
Online data privacy is crucial because it puts you in charge of your personally identifiable information. When you lose this control, anyone with the motive and means might use your identity for their purpose, whether selling you an expensive gadget you don’t need or robbing you of your funds.
Common Threats to Your Online Privacy
Both major and minor things compromise your online data security. These online threats add up. Let’s go through some of the most prevalent threats that continuously jeopardize your data privacy.
Weak or Reused Passwords
We’ve all been guilty of using weak passwords at some time. Some even use the same password to sign up on multiple platforms. People still commonly keep weak passwords like “123456” or “guest,” allowing hackers to crack them in seconds.
The primary culprit of the large data breaches you read about in the news is the reuse of weak passwords. This is because it enables cyber criminals to simultaneously break into several accounts, access private information, or commit financial fraud.
Social Media Data Harvesting
Your social media content is aggregated and analyzed to identify patterns and trends. Privacy on social media has been in limbo since a series of scandals like the Cambridge Analytica story took place, in which data was exploited to sway voters, cyberbullying, and publishing personal information publicly.
Major social media platforms have also had data breaches, exposing the personal data of millions of users. The most recent data breach at Facebook exposed the personal details of 533 million users, including their names, contact numbers, addresses, date of birth, bios, and email addresses.
Search Engines User Tracking
Search engines track your search history and the websites you’ve visited. Your entire browsing history is recorded if the search engine provider also functions as a browser.
Traditional search engines collect your activity, including search history, cookies, IP addresses, and click-through history, to build a customer persona based on your buying preferences, location, and more.
These customer personas are valuable to advertisers as they come in handy in personalizing ads, which is why they are sold to advertisers and third-party companies for profit.
Unsecured Web Browsing
Whether you realize it or not, web browsers are the most used app on your computer or mobile phone. The default browser is the bridge that connects you to the internet every time you visit a link or conduct an online search. You might have even allowed it to save your passwords.
Cybercriminals are well aware of this and utilize many tactics like malicious extensions, corrupted ads, unsecured links to shady websites, and more.
Downloading Malicious Files
You can be vulnerable to a potential cyberattack if you mistakenly download a malicious file onto your computer or mobile device and you don’t install antivirus software.
Once the malware has access to your system, criminals can exploit it to steal sensitive data, send you unwanted or inappropriate ads, demand money to decrypt data locked by ransomware, and leave your system open to further malware infection.
Cyber-Attacks
To trick you into clicking, tapping, downloading, and opening their traps, malicious hackers combine their technical prowess with psychological manipulation. They lure you into clicking links in deceptive texts sent to your phone (smishing), opening malicious emails (phishing), or even calling you over the phone to get personal data (vishing).
These cyber-attacks usually come with keyloggers, which are malicious programs that record everything you input on your device and gather your login credentials. This information is later used to rob you, access control over private data, or make your life miserable.
Most cyber-attacks are automated in that they only look for targets with unsecured accounts, apps, and devices, which are simple to break into for easy exploitation.
Identity Theft
Identity theft was a crime long before the internet was even a thing. However, technological advancement has created new possibilities for scammers, even if you’re using a recommended identity monitoring service. It occurs when fraudsters access enough information about someone’s identity to impersonate that person.
This information could include name, date of birth, social security number, driver’s license, bank account details, or anything else.
Hackers could access customer data using the cyberattack tactics described in the previous section, such as phishing, malware, and smishing.
Methods to Enhance Your Online Privacy
If you’ve made it this far, you presumably better understand how much of your online privacy is at risk. You might ask yourself, “How do I protect my data privacy online?”
Well, online privacy is nothing to worry about. Simply being aware of the general data protection regulation will help you develop good online habits like the ones mentioned below.
Remove your Existing Personal Data Online with DeleteMe
Today, almost everything we do online is monitored. When you inquire about health insurance portability, get a mortgage, apply for a credit card, or download a new app, your personal information is gathered and sold.
Data brokers are companies that collate this information like names, home addresses, birthdays, phone numbers, social security numbers, marital status, court records, and more to sell or license it out to other businesses.
Along with this growth of data brokers, there are also now plenty of companies that erase your data off the internet.
DeleteMe is one of the best options to help you to delete personal data collected by over 750 data brokers. I’ve been using them for years and as you can see below, they’ve created much better digital privacy for me by removing data in numerous places.
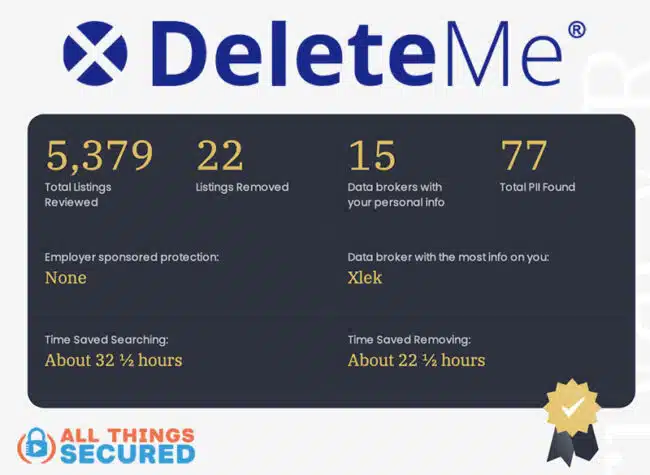
You can use DeleteMe’s free DIY opt-out procedures to manually request that these broker sites remove your data, and they are obliged by data privacy laws to comply, but it’s a tedious process. DeleteMe takes care of it for you.
*Use promo code “ATS” for 20% off
Employ Strong, Distinctive Passwords and Two Factor Authentication
To tighten the security of your social media accounts and devices, you need to deploy secure and unique passwords on each.
The most secure passwords are a mix of numbers, letters, and special characters. For most people, the best option is to use a good password manager to create and store these on all your devices. Password managers are simple to use and very cheap.
Also, it’s critical to use two-factor authentication (2FA) on accounts that allow it. It acts like an extra security layer that requires two separate, distinct forms of identification.

Update Your Privacy and Security Settings
Whether it’s your mobile device, your laptop computer or even social media sites, the default privacy and security settings usually aren’t good enough. Facebook is a great example here (here’s how to update Facebook privacy settings).
In order to protect your online privacy, you need to change a lot of these settings to be more privacy-friendly and respect what is your private information.
Commit to Sharing Less Online
Anyone who has seen “You” on Netflix knows how easy it has become for predators like Joe to peak into the private lives of anyone through their social media profiles.
Oversharing exposes more sensitive personal data and information about you to nefarious bystanders than you’d ever want to reveal.
They can acquire a complete map of your possessions by inspecting the home video footage you shared on Instagram. Similarly, images of your boarding pass can reveal your travel destination and the length of your stay.
Delete Unused Mobile Apps and Browser Extensions
Older apps you haven’t updated in a while can harbor significant security flaws, so eliminating them is best. The more programs or apps you have on your device, the greater the chance that one of them could be compromised.
Furthermore, it’s best to download apps directly through a trusted source like the app store or Google Play store. Make sure you verify the permissions that the apps require.
Similarly, browser extensions that you no longer use should be deleted permanently to safeguard your data and enhance the device’s performance.
Block Search Engines from Tracking You
The most commonly used search engines, like Google and Bing, collect a lot of personal data about their data subjects. They can track all your activity because they run the well-known browsers Chrome and Edge, respectively. Private browsing simply isn’t possible when using these browsers.
So, if you’re serious about being anonymous on the internet, switch to a more privacy-focused browser like Brave or consider downloading ad blockers.
Browsing Online With a Secure VPN
A VPN, or virtual private network, encrypts your traffic and hides your IP address from outsiders. We at All Things Secured advocate using a reliable VPN to achieve a safe online experience.
A VPN is worthwhile if you often use public Wi-Fi networks, especially if you’re going to log into sensitive online accounts. Similarly, VPNs provide various security features like IP/DNS leak protection and a kill switch. As a result, even your Internet Service Provider (ISP) woun’t be able to monitor your online activity.
If you’re searching for a reliable VPN, here are our top five picks for the Best VPNs for online privacy.
Keep Your Software Up-to-Date
You don’t want to ignore software updates! Hackers are notorious for exploiting known vulnerabilities that have previously been resolved. They find it easier to break into computers with outdated software that haven’t installed the fix.
To avoid missing out on crucial features and security patches, keeping all your software, including operating system, browser, and programs, up to date is best advised.
Disable Ad Personalization and Data Tracking
Most of your personal information is collected online for marketing purposes so that you may see ads you’re interested in. Although data privacy law allows this, you can take a few security measures to disable this kind of online tracking.
Every time an app wishes to track user activities, iOS users are prompted with a pop-up; you must always decline such requests. Additionally, wherever feasible, turn off cookies while visiting any website.
Thanks to recent data protection laws like the California consumer privacy act, you can also opt out of ad personalization on major platforms, including services from Google, Apple, Facebook, Twitter, Microsoft, Amazon, etc. These online services must maintain data privacy compliance.
Always Double-Check Any Unfamiliar Links
Don’t click on links that take you to shady or fraudulent websites; otherwise, you risk falling victim to a phishing scam and handing over your personal information to a scammer.
This is true of emails and text messages, but this also means it’s important to use official app stores to keep from downloading malicious software.
Online privacy often starts with training yourself and family members how not to fall for these kinds of scams.

Frequently Asked Questions
Let’s now answer some of the most frequently asked questions about online security and online privacy.
No! Although it appears so since internet privacy has greatly diminished but that isn’t the case. There is no “privacy by default”, but you have the option to create better privacy online through private browsing, antivirus software and better privacy habits.
Google search results are difficult to remove. You have the right to request the removal of personal information, particularly with data brokers such as Whitepages. For general websites, removing the search results requires contacting the website that has that information and making a removal request.
Yes. The time it takes to protect your privacy online may seem like a lot, but in the end it is worth it. Once you lose privacy, it’s very difficult to get it back.
Neither option gives you more privacy, but as far as security goes, it’s harder to get attacked with SIM swapping if you use an eSIM. Here are some of the most popular international eSIM options.

