Two-factor authentication (2FA), also referred to as multi-factor authentication (MFA), is a method by which an institution, website, social media platform or other application verifies your identity beyond the first of step of using your password. Here’s what you need to know about how it works and three ways that you can easily set it up to secure yourself online.

While you should already be using a secure password, 2-factor authentication is an added layer of security to make sure that even if somebody where to gain access to your password, they still wouldn’t be able to log into your bank, email or other account.
When used in conjunction with a quality password manager app and proactive identity monitoring services, these added layers of security can dramatically decrease your risk of being hacked or having your identity stolen.
In short, it’s a very good security measure and one that I recommend you employ. I’m going to break this explanation down into three different parts:
Below I’d like to give you an idea of how 2-factor authentication works and how you can start using it today.
Note: Some of the links in this article may be affiliate links, which means that at no extra cost to you, I may be compensated if you choose to use one of the services listed. I only recommend what I personally have used, and I appreciate your support!
How Two Factor Authentication Works

Two factor authentication is a security measure that has been employed by tech companies for many years now to make sure that no outsider gains access to the internal network.
The basis of how 2FA works goes like this:
- Your username and password are static (i.e. you set them and they rarely change);
- Two-factor authentication is dynamic and/or physical. This means that either the code changes for every login or you have a physical key that you need to use to login.
- Using both provides an added level of security.
It may sound complicated, but the good news is that this kind of security technology is very accessible to the average internet user…
…and that includes YOU!
Multi-factor authentication is fast becoming the standard for all online logins and it is something you SHOULD use if you can. There are different types of 2FA you can use.
Different Types of 2-Factor Authentication
When you hear the term “2-factor authentication,” it may be a bit confusing at first. The reason is that this form of security is implemented in a number of different ways.
Let’s take a look at the most popular ways that companies are deploying 2-factor authentication (also known as 2FA):
Text Messages as 2-Factor Authentication

One of the original methods of 2-factor authentication is the SMS text message.
Setting up text message 2FA requires you to give the company your phone number and allow them to text you a verification code when you log in.
Once enabled, text message 2FA goes like this:
- Sign into your account using your password. Instead of logging in, you’ll be directed to a page that asks for an additional code.
- A numeric code will be sent to your phone as a text message.
- When you receive the text, enter the code when prompted to get access to your account.
Unfortunately, text-based 2FA isn’t a fool-proof method of securing your accounts. A new attack known as “SIM swapping” hit even the CEO of Twitter in 2019.
Authenticator App for 2FA
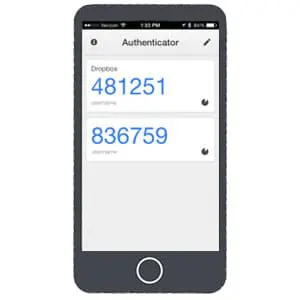
Another popular – and frankly more secure – method of 2-factor authentication makes use of what are known as authenticator apps.
The standard for this kind of security is Google Authenticator (I even created a guide for how to set up Google Authenticator).
Unfortunately, Google Authenticator is no longer a secure 2FA option, but there are plenty of others that are available to download.
To set up any 2FA app, you’ll be required to download the app on your phone and scan a QR code. At this point, the process goes like this:
- Sign into your account using your password. You’ll be directed to a page that asks for an additional code.
- Open your authenticator app and find the 6-digit code.
- Enter that code when prompted to get access to your account.
This method of account security is harder to hack. However, as with all security, there’s the added step of opening up another app on your phone and copying the numeric code before the timer changes it.
Security Keys for 2-Factor Authentication
The most secure method of 2-factor authentication is the security key (such as the Yubikey).
While it’s common within tech companies to use security keys, it’s only recently become popular among the general public.
Setup for security keys is a bit more technical, but once complete, it makes life much easier. The process is simplified to look like this:
- Sign into your account using your password.
- As long as you have your security key on your keychain (for phones) or plugged into your USB port, you’ll immediately get access. No need for codes or additional steps.
In this scenario, nobody is able to log into your account unless they have both your password and your physical security key. There are different kinds of keys, so check this comparison chart of 2FA keys from Yubico.
Again, no single method is foolproof, but it’s certainly the next step of added security for your important accounts, which I’ll detail below.
Recommended Uses for 2-Factor Authentication (TODAY!)
The 2-Factor Authentication method is being used by a growing number of companies including financial institutions, social media platforms and many other online applications.
You can find a comprehensive list of websites and apps that allow for 2FA, but for the sake of this article I’d like to give you a list of the most important areas where you should consider using 2-factor authentication today.

- Your Email: Set aside time to enable 2-factor authentication for email before it’s too late. This added layer of security is available for Gmail, Hotmail, Yahoo, Office 365 and many other popular email providers. If your email service provider doesn’t offer 2-factor authentication, honestly, it’s time to start migrating to a new email.
- Your Financial Institution: Unless you still live in the stone age, you probably manage your bank account online. All major banks allow – and even encourage – their customers to enable 2-factor authentication. Go into your security profile and set it up.
- Your Social Media Platforms: Whether you use Facebook, Twitter, Pinterest, Instagram or others, it’s possible to enable 2-factor authentication on all of them. The biggest hurdle is figuring out how to turn it on, which usually requires users to go into their account’s advanced settings.
- Wherever You Store Sensitive Data: Do you host websites? Do you upload documents to Dropbox or Evernote? Wondering if Google Drive is secure? Think about areas of your online existence where a stolen password could be a big problem. Most of the time, these services will offer 2-factor authentication. If they don’t, I suggest you find an alternative service.
- Wherever Available: Frankly, if 2-factor authentication is an option, you should use it. One of the things I love about my 1Password password manager, is that it alerts me if 2FA is available for a login and I haven’t already set it up.
Inconvenience is the New Standard of Security
Here’s a quick tip for you.
In a world where we value ease and expediency, inconvenience is the new standard of security.
What do I mean by that?
Well, if I’m really honest, I have to say that it’s quite inconvenient to have to wait for a text message or log into my Google Authenticator just so that I can check my account balance at my bank.
It’s annoying when all I want to do is check my email on my computer.
The desire to eliminate those inconveniences is exactly what is going to make you vulnerable with your online security.
Yes, 2-factor authentication is inconvenient.
Hopefully, as the adoption of security keys grow, authentication will become much easier.
In the meantime, I highly suggest you swallow your frustration and endure the annoyance. It’s the new standard of security.
Final Thoughts on 2-Factor Authentication
If you’re reading this right now and you haven’t yet enabled 2-factor authentication, please stop and do that…
…right now.
Take advantage of this extra layer of security for your email, banking, social media and online data storage. It only takes a few minutes to set up and it could make a world of difference for you online.
Remember, though: this is an added layer of security.
You still need to check if your passwords are strong and if you’re connecting to public wi-fi (coffee shop, airport, etc.), make sure that you use a VPN to encrypt your data.
Using 2-Factor Authentication is just one step towards Online Security. To take six more steps read 7 Absolutely Free Online Security Tools.
Be sure to subscribe to the All Things Secured YouTube channel!








If I use an authenticator app on my phone, how to I log on to a URL via my phone?
Thanks,
Steve
In some cases, I am able to open up the authenticator app, remember the code and switch back over to the app or browser where the code is being requested. The easier way, however, is to use a password manager app that integrates OTT (such as 1Password). It will actually copy the code to your clipboard when you need to use it.