Password strength meters are used quite often nowadays as a way to judge how secure your online login is. You’ll find these meters when you’re creating a new online login, where some websites won’t even let you sign up if the password is considered too weak. But how effective are these password meters? The truth is, they’re flawed…and here’s what you need to know.

For the time being, passwords are still the primary defense any attacks against your online accounts.
The stronger your password, the stronger your defense.
There are three levels of password security, and which you choose is based on your personal needs. So when you’re creating a new online account and a password strength meter tells you that it’s “strong”, the assumption you make is that your online security is, in effect, strong.
Right?
However, if these password strength meters are flawed, that’s something worth paying attention to.
Below I’m going to walk you through exactly what makes these meters flawed, what this means for you, and how you can best respond.
Weakness of Password Strength Meters
While there are definitely weaknesses in even the best password strength checkers, what we’re specifically referring to here are the strength meters that you find when you’re signing up for a new online account.
They usually look something like this:
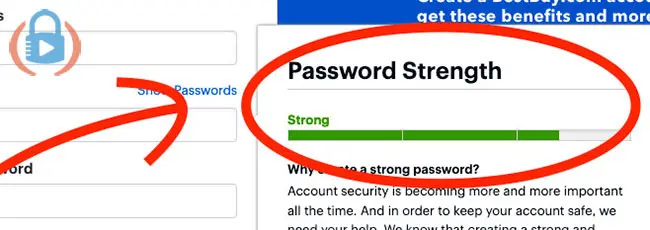
As you create the new account, you’ll be asked to create a username and passcode (and then confirm the password).
A strength meter will show up telling you whether what you type is “very weak”, “weak”, “strong” or “very strong”.
The problem is that these security tools are nothing more than lines of code that are forced to make a few flawed assumptions that might lull you into a false sense of security.
Flawed Assumptions of Strength Meters
What are some of these flawed assumptions these password strength meters make and how could they affect your password security?
Let’s look at a few major assumptions here:
- You Haven’t Used This Password Elsewhere: A checker or strength meter has no way of knowing whether what you type is a unique passcode or one you’ve used for every online account you have. If it’s been used elsewhere and that database is hacked, that “strong” password is now very “weak”…but a meter won’t know that.
- You Aren’t Using Personal Information: Algorithmic meters can only judge strength based on brute-force attacks (i.e. trying every known combination of words/letters/characters). It doesn’t know if you’re using your maiden name, your birthday, your dog’s name, etc. But a hacker probably will, and they can program their attacks to prioritize those words/numbers as they hack your account.
- All Password Guesses are Equally Good: Again, these password meters have to make assumptions based on mathematical equations. In the real world, hackers have access to literally millions of common passwords based on exposed user data. Trying these first usually reduces the amount of time it takes to unlock a passcode-protected login.
Even password checkers are not all the same.
You want to find one based on an algorithm that goes beyond just entropy (how long it would take to brute-force attack a login) and weighs your passcode against common password lists, names, popular words and other patterns.
That’s why I recommend you try our free password strength checker here.
What Does This Mean for Your Passwords?
If password strength meters are flawed, what does this mean for you?
Well, to begin, it’s worth noting that research shows strength meters do succeed at encouraging people to create stronger passcodes than they would have if the meter were not present.
But “stronger” is still not as good as “strong” when you’re dealing with things like your bank account and your email address.
Understanding the flaws in a strength meter means two things for you:
- You should take the meter results with a grain of salt;
- You should find alternative ways to verify the strength of your passwords;
That second one is what I want to focus on here for a moment.
How to Protect Your Password Security in 2023
Now to the important part:
What can you do to make sure that the flaws in these strength meters don’t affect your personal online security?
There are three primary ways that you can combat the flaws and bad assumptions in password meters.
Method 1: Use a Good Password Generator
Instead of relying on various mnemonic methods or memorized patterns, using a solid passcode generator can be a great way to create strong passwords if you do it right.
These generators can be found online or as an add-on to your browser. You’ll see an example here:
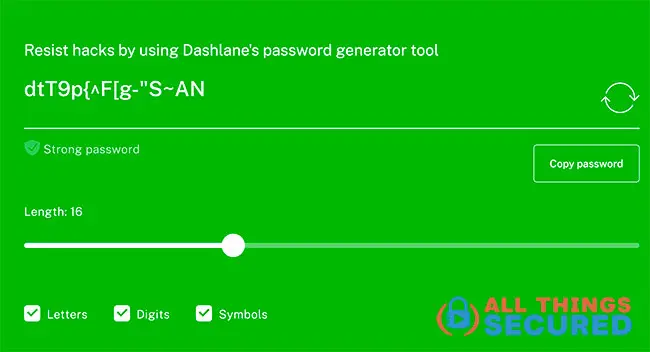
The only problem here is that you not only have to generate these strong passwords, you also have to remember them.
There’s a way to fix this that I’ll cover in method 3. But first…
Method 2: Use 2-Factor Authentication
One of the absolute best ways to fortify your online security defenses is through what’s known as 2-factor authentication.
Two factor authentication (often shortened to “2FA”), is an added layer of security that forces you to verify your identity a second time after a correct password is entered.
This can be done via:
- A code that is texted to your phone number;
- A 2FA authenticator app on your phone that gives you a code;
- A security key like the Yubikey that you plug into your computer or phone to verify who you are;

If you follow no other takeaway from this article than to start using 2FA, you’ll be doing well. I’ve even done a short tutorial on how to set up Google Authenticator for you.
This is one of the best things you can do for your online security.
Method 3: Using a Password Manager App
Finally, one of my favorite ways to bypass the flaws in most strength meters is to use a password manager app.
While I do have my preferred password manager apps, I don’t want you to think that I’m writing this just to make money off of you, so I’m not going to list them here.
Just know that a manager app not only helps you generate strong passcodes, it also stores them for you behind a “master password” that only you know.

But what if someone cracks my master password?! Won’t they then have access to all of my accounts?
I hear this a lot, and it’s a reasonable question.
My answer is twofold:
- Make your master password the best one you have;
- If you’re still worried, use the double-blind password strategy so that even if your manager app vault were hacked, it’s still useless.
Final Thoughts on Password Strength Meters
The bottom line is this: relying on a password strength meter as the only way to verify how strong your online defenses are is foolish.
They are flawed, and they work on assumptions that may or may not be true for you.
Instead, you should be using passcode generators, 2-factor authentication and even a manager app to make sure that your online logins are as strong as they need to be. It’s only one step, but it’s an important one as you start to secure your online identity.
We’re dealing with some important online accounts here…
…this isn’t something to leave for another day!
You wouldn’t leave your house unlocked. You rarely leave your car unlocked. Why would you consider doing that for your bank account or email by relying solely on a strength meter?





Leave a Reply