Is there such a thing as a zero log VPN? The short answer is no, there isn’t. In fact, these companies are flat out lying to you when they claim they are a no logs VPN. That’s the bad news. The good news is that the more you understand VPN logging, the better prepared you can be […]
2FA vs MFA | Is Two-Factor or Multi-Factor Authentication Better?
When accessing sensitive information online, we want to make sure that everything we interact with is safe, secure, and protected. Whether for personal or business use, it’s important to consider additional access security, when deciding between 2FA and MFA. Logging into a website creates a traces of your digital footprint. While this doesn’t typically affect us […]
Can Virtual Credit Cards Improve Online Privacy?
It’s not uncommon for us to give out our credit card information over the phone, over email and on pretty much any online shopping portal that asks for it. It’s often necessary…but is it secure? Here’s a look at a privacy-focused alternative known as virtual credit cards, a service that promises consumers the kind of […]
STOP Using Mobile Spy Apps (they’re dangerous…here’s why)
It’s tempting to think that mobile spy apps are the answer to the problem you’re having monitoring your kid, your spouse or your employee. But before you sign up for a spy app, you need to consider the associated risks. In this article, we’re going to explain exactly why you should avoid most spy apps […]
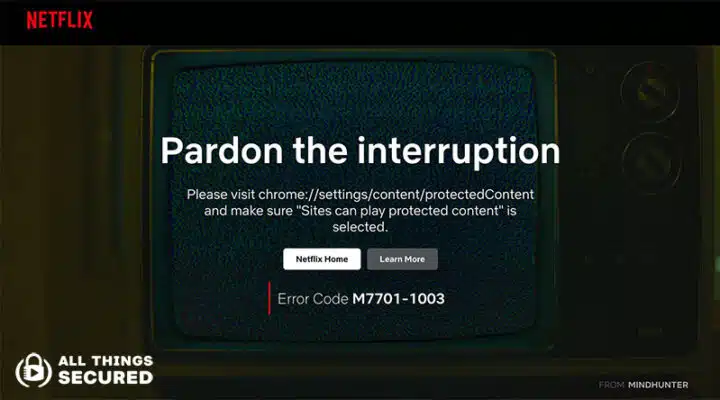
How to Stream Netflix on Brave (“Brave can’t play Netflix!”)
If you’ve migrated over to the Brave browser and you’ve come across a “Pardon the interruption” error code while trying to stream Netflix, HBO, Amazon Video or any other content platform, you’re not alone. Here is the simple, 30-second change you need to make in the settings to fix the problem when Brave can’t play […]
What is Split Tunneling VPN? (and is it actually secure?)
VPN Split Tunneling is a feature that allows users to direct a portion of their internet traffic through an encrypted virtual private network while leaving the rest to be routed through a separate tunnel on the open network. It’s an advanced feature with specific uses that we’ll cover in detail here. By default, a virtual […]